Hi Thillai,
Upon closer examination of the logs you sent, it
appears that the code execution flow in both cases
is not the same, and the errors encountered are of a
different nature.
My previous message was based on Use Case 10,
which seems to correspond to a transaction involving
two readings of the SFI=14h file. However, the log
for this case does not display DEBUG level traces,
which would be very helpful for a more in-depth
analysis.
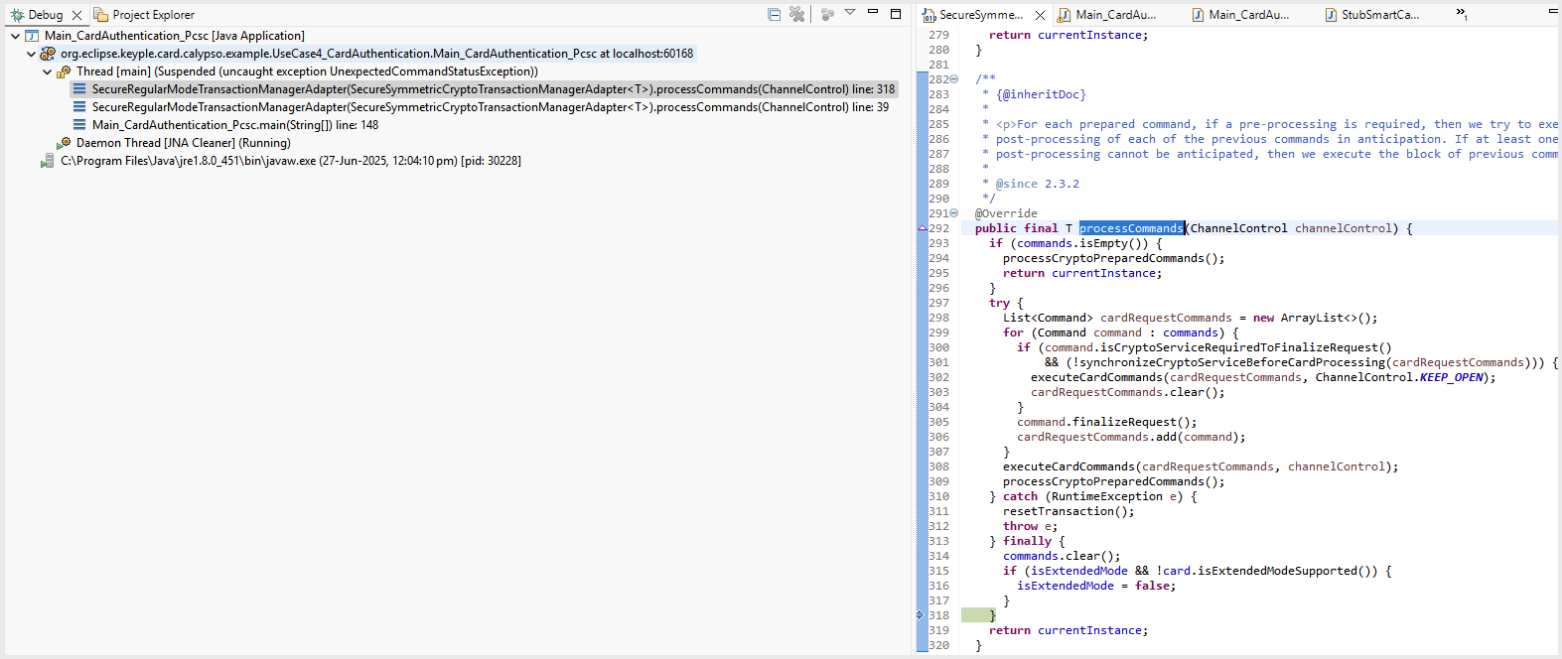
On the other hand, the log for Use Case 4 does
show DEBUG traces, but here the transaction
concludes with an "Unauthorized key error." This
specific error suggests that the card you are using
requires a particular configuration to specify the
key KIF value that is not provided by this
particular card.
Based on the JSON file generated by the card
analysis tool, the KIF value to be used for this
AID is 0xFF. In the context of the Use Case 4 code,
this would translate to an adjustment within the
`initSecuritySetting()` method, similar to the
following:
private static void
initSecuritySetting() {
LegacySam sam =
selectSam(samReader);
symmetricCryptoSecuritySetting =
calypsoCardApiFactory
.createSymmetricCryptoSecuritySetting(
LegacySamExtensionService.getInstance()
.getLegacySamApiFactory()
.createSymmetricCryptoCardTransactionManagerFactory(samReader,
sam))
.assignDefaultKif(PERSONALIZATION, (byte)
0xFF)
.assignDefaultKif(LOAD, (byte) 0xFF)
.assignDefaultKif(DEBIT, (byte) 0xFF);
}
Could you please try implementing this change in
your Use Case 4 code and observe if it resolves the
"Unauthorized key error"?
Regarding use case 10, I would need more logs to
help you. But the previous configuration with 0xFF
should also apply here!
Best regards,
Jean-Pierre Fortune
Keyple-Dev Team