|
Rolf,
Indeed if I look at the two executables in the following:
https://download.eclipse.org/eclipse/updates/4.12/R-4.12-201906051800/binary/org.eclipse.platform.sdk.executable.win32.win32.x86_64_4.12.0.I20190605-1800
They do not show signature properties
when extracted, so p2 installing these (p2 director via the
installer or via p2 update) would not produce something with a
signature in would appear.
I would have expected this file to
contain two signed executables, but that appears, as you suggest,
not to be the case. :-(
I asked Dani just now, and he also
expected these would be signed...
On 18.06.2019 16:13, Rolf Theunissen
wrote:
First of all, the properties of the executable show it very
clearly.
Second, https://bugs.eclipse.org/bugs/show_bug.cgi?id=509799#c4
this comment.
eclipse.exe properties from Eclipse IDE for Java Developers
Package
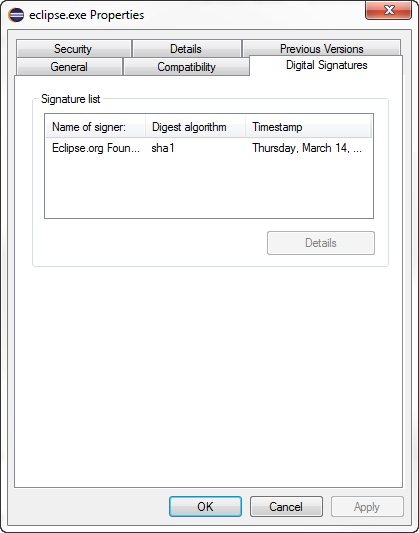
Eclipse properties for product installed via oomph.
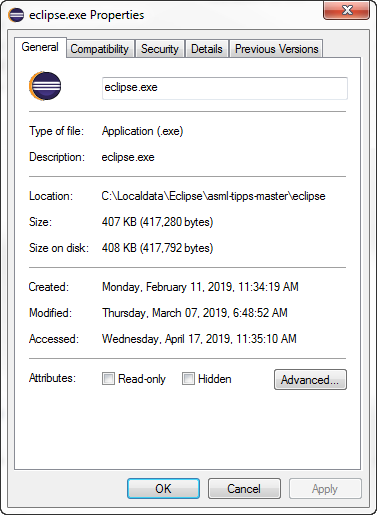
Op 6/18/2019 om 4:04 PM schreef Ed
Merks:
Rolf,
I don't believe what you suggest is the case. The
eclipse.exe in the p2 repository, like all the artifacts in
the repository, is signed. Otherwise, if one did an update
and the executable needed to be updated, it would be updated
with an unsigned version, which would not be acceptable. What
makes you think/assume that these are not signed?
On 18.06.2019 15:56, Rolf
Theunissen wrote:
Hi,
I came across the bug below. What triggered me from the
comments on Bug 509799 is, that the 'eclipse.exe' is
apparently signed as part of the EPP build. As we are
pushing Eclipse-Installer now, many installations contain a
'eclipse.exe' that is not signed.
So maybe the problem is not how to let Microsoft trust the
Eclipse Signature, but more how to ensure that the
'eclipse.exe' is signed on all installations.
Bug 539954 - eclipse installer
"SimRel 2018‑09" from ibm cloud is reported as virus
infected
Bug 509799 - Symantec reports a
Trojan SONAR.AM.C!g24 in eclipse
Bug 485899 - upgrading eclipse causes
anti-virus to alert
Rolf
Op 6/17/2019 om 8:35 PM schreef
Tim Webb:
Unfortunately a no-go. Gave it a try and
despite taking 1.5 minutes to run the command line, it
still took the full first scan after running the exe that
had already been scanned.
It seems we'd need some guidance from Microsoft in
how to get some/all of Eclipse whitelisted in their
Security Intelligence. Perhaps at least major releases
can have their Jars registered...
C:\Users\tim>"%programfiles%\Windows
Defender\mpcmdrun" -AddDynamicSignature ...
You need administrator privilege to execute this
command.
Perhaps there is a way we can register the signature
and have the Eclipse Installer ask the user for
permissions to invoke registering the Eclipse Signature
as an approved certificate?
Tim
Can you make one of
the affected persons try running this before they
start eclipse?
"%programfiles%\Windows Defender\mpcmdrun" -scan -file
"full_path_to_eclipse_installation"
If that helps, we could potentially add this to the
installer (but not
the ZIPs, of course), in the hope Defender afterwards
remembers it
already scanned the installation. However, I have no
experience with the
above, I just googled around for cmd line interaction
with defender.
There are also more options (like different scan types),
not sure if
that makes an additional difference.
Another potential issue to check: Windows marks
downloaded files
automatically as "unsafe". See
https://www.howtogeek.com/70012/what-causes-the-file-downloaded-from-the-internet-warning-and-how-can-i-easily-remove-it/
for an instruction of how to remove that marker from
many files. I'm not
sure if this really has any relation with Windows
defender scans, I
think it only triggers the "Do you really want to..."
popup.
That all being said, at our company we have given up to
find something
better than filters as workaround. With TrendMicro
Antivirus on access
scanning being active, every git operation inside
eclipse is about 10
times slower than with eclipse filtered from the scan.
Ciao, Michael
_______________________________________________
platform-dev mailing list
platform-dev@xxxxxxxxxxx
To change your delivery options, retrieve your password,
or unsubscribe from this list, visit
https://www.eclipse.org/mailman/listinfo/platform-dev
--
Cheers,
Tim
Timothy R. Webb
Vice President,
Operations
_______________________________________________
platform-dev mailing list
platform-dev@xxxxxxxxxxx
To change your delivery options, retrieve your password, or unsubscribe from this list, visit
https://www.eclipse.org/mailman/listinfo/platform-dev
_______________________________________________
platform-dev mailing list
platform-dev@xxxxxxxxxxx
To change your delivery options, retrieve your password, or unsubscribe from this list, visit
https://www.eclipse.org/mailman/listinfo/platform-dev
_______________________________________________
platform-dev mailing list
platform-dev@xxxxxxxxxxx
To change your delivery options, retrieve your password, or unsubscribe from this list, visit
https://www.eclipse.org/mailman/listinfo/platform-dev
_______________________________________________
platform-dev mailing list
platform-dev@xxxxxxxxxxx
To change your delivery options, retrieve your password, or unsubscribe from this list, visit
https://www.eclipse.org/mailman/listinfo/platform-dev
|


